Creating a Contact Tracing Scanner using Web Bluetooth
I have recently been looking at the Contact Tracing specifications Apple and Google released earlier this year in aid of the fight against COVID-19. Looking through these documents allowed me to grapse how the system was put together, and ease fears family members had with regards to how privacy conscious the Exposure Notification system is.
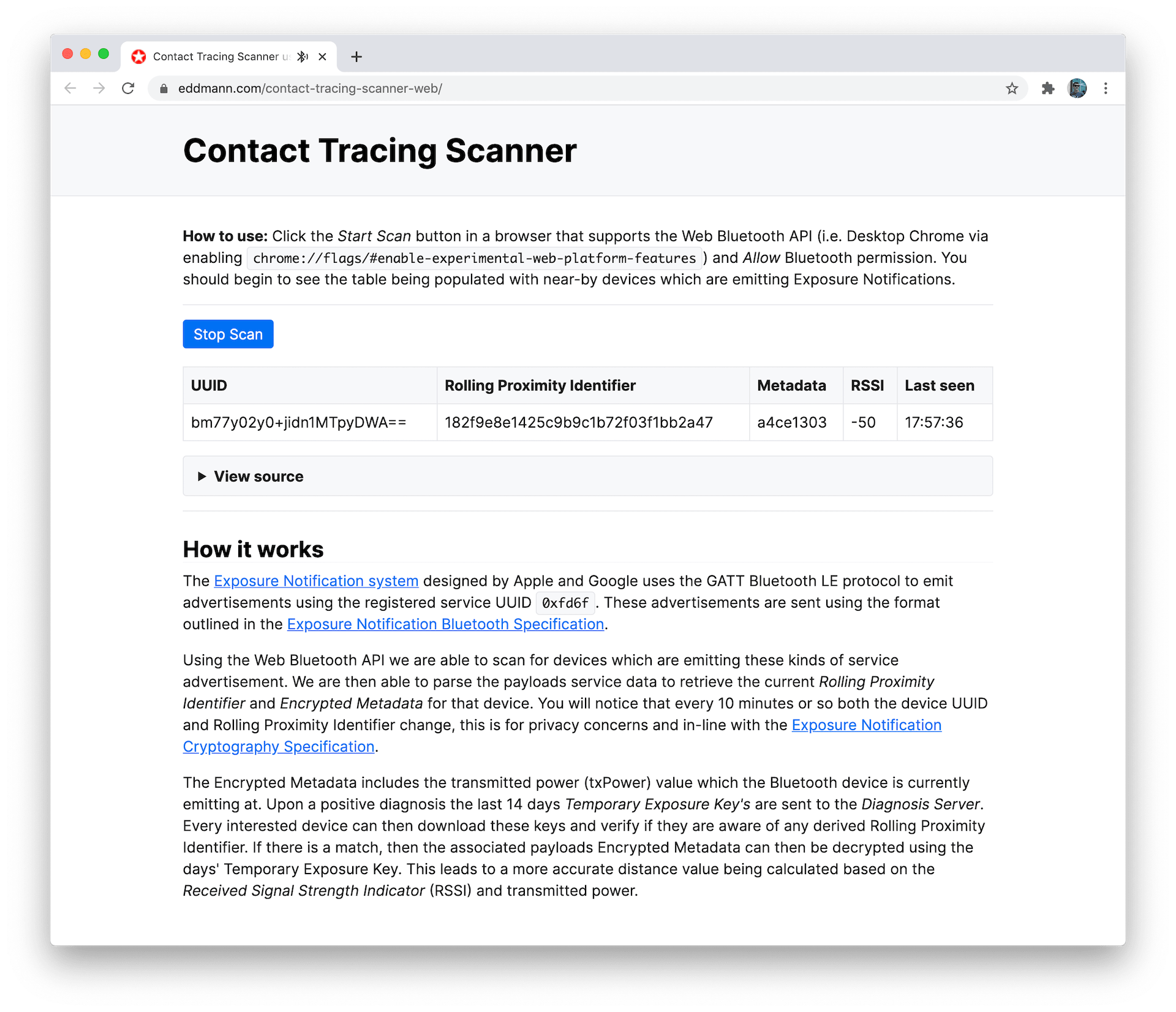
I decided to make a Web Bluetooth-based scanning application which highlighted what an Exposure Notification-enabled device actually emits.
How it works
The Exposure Notification system designed by Apple and Google uses the GATT Bluetooth LE protocol to emit advertisements using the registered service UUID 0xfd6f.
These advertisements are sent using the format outlined in the Exposure Notification Bluetooth Specification.
setActiveScan(
await navigator.bluetooth.requestLEScan({
filters: [{ services: [0xfd6f] }],
keepRepeatedDevices: true,
})
);
Using the Web Bluetooth API we are able to scan for devices which are emitting these kinds of service advertisement. We are then able to parse the payloads service data to retrieve the current Rolling Proximity Identifier and Encrypted Metadata for that device. You will notice that every 10 minutes or so both the device UUID and Rolling Proximity Identifier change, this is for privacy concerns and in-line with the Exposure Notification Cryptography Specification.
const onAdvertisementReceived = event => {
const serviceData = event.serviceData.get(event.uuids[0]).buffer;
setDevices(devices => ({
...devices,
[event.device.id]: {
uuid: event.device.id,
rollingProximityId: toHex(serviceData.slice(0, 16)),
metadata: toHex(serviceData.slice(16)),
rssi: event.rssi,
lastSeen: Date.now(),
},
}));
};
The Encrypted Metadata includes the transmitted power (txPower) value which the Bluetooth device is currently emitting at. Upon a positive diagnosis the last 14 days Temporary Exposure Key’s are sent to the Diagnosis Server. Every interested device can then download these keys and verify if they are aware of any derived Rolling Proximity Identifier. If there is a match, then the associated payloads Encrypted Metadata can then be decrypted using the days’ Temporary Exposure Key. This leads to a more accurate distance value being calculated based on the Received Signal Strength Indicator (RSSI) and transmitted power.